The work we do includes the management and reduction of cyber security risk, to ensure the protection, integrity and availability of digital services and data. This work helps to attain and support delivery of Aberdeen 2040 objectives.
The University of Aberdeen Information Security Policy and Information Security Supporting Policies support this purpose and provide guidance on the responsibilities, requirements, and principles which are necessary for us to achieve this.
The IT Conditions of Use for using Information Technology facilities and supporting summary video provide information on the responsibilities of the University community. These conditions are in place to ensure University digital services and computing facilities are used for their intended purposes in safe, lawful and equitable ways.
- Mandatory Information Security Awareness Training
-
Mandatory Information Security Awareness Training
You are our best line of defence.
Because cyber attacks come in many forms and are constantly evolving, it's important that you keep up to date and that you know what to look out for.
To help you do this, we have launched online Information Security Awareness training using the MetaCompliance platform.
Featuring videos, audio scripts, and animations, and covering:
- Email, Phishing and Internet
- Passwords
- Social Media
- Remote Working
The training is mandatory for all staff and PGR students and is required to be completed annually.
You can work through the modules at your own pace over multiple sessions, picking up where you left off. And once you've completed the training, you can dip back in at any time to refresh your knowledge on a particular topic.
- Access the training at: https://cloud.metacompliance.com/
- When prompted enter your UoA email address and click Next
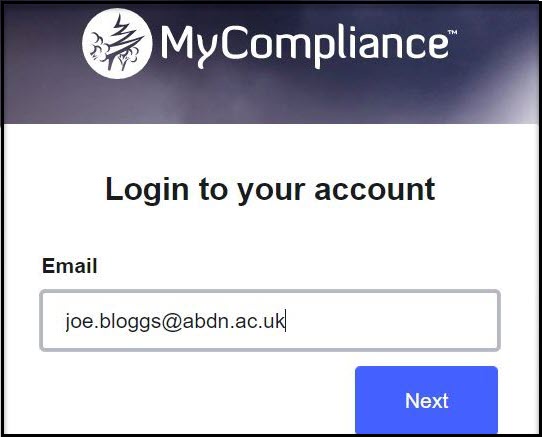
- And when prompted enter your UoA username and password
Further help and advice
For help and advice contact IT Services via MyIT myit.abdn.ac.uk or email: servicedesk@abdn.ac.uk .
IT Security. We are all responsible.
- Phishing Email - How to report
-
What is phishing?
Phishing emails are by far the most common initial entry point for cybercriminals seeking to carry out major attacks, including ransomware. They can also lead to significant personal impact, including financial loss.
Phishing is when criminals attempt to trick people into doing 'the wrong thing', such as clicking a link to a dodgy website.
Phishing can be conducted via a text message, social media, or by phone, but the term 'phishing' is mainly used to describe attacks that arrive by email.
Criminals send phishing emails to millions of people, asking for sensitive information (like bank details), or containing links to bad websites. Some phishing emails may contain viruses disguised as harmless attachments, which are activated when opened.
How do I spot a phishing email?
- Many phishing attempts will try and create official-looking emails by including logos and graphics. Is the design (and quality) what you'd expect?
- Does the email contain a veiled threat that asks you to act urgently? Be suspicious of words like 'send these details within 24 hours' or click here immediately'.
- Look at the sender's name and email address. Does it sound legitimate, or is it trying to mimic someone you know?
- Hover over any links and you can see the website it will take you to. Does it look legitimate?
- If it sounds too good to be true, it probably is.
How do I report a phishing email?
If you receive a suspicious message, just look for the Report Phishing button.
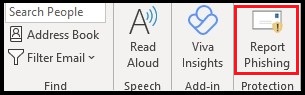
How to report from the Outlook Client App
With the email selected just look for the Report Phishing button (in the Protection section of the Home tab of the Outlook ribbon):
How to report from Outlook Online (OWA)
Select the email and click the Report Phishing button found on the ribbon.
Here's what to look for:

How to report from the Outlook Mobile App
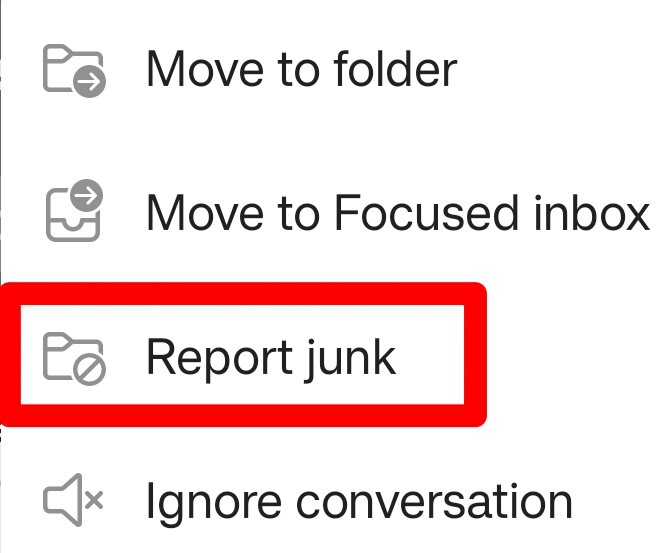
Open the message and expand the options menu (three dots at top right of window):
Tap Report junk
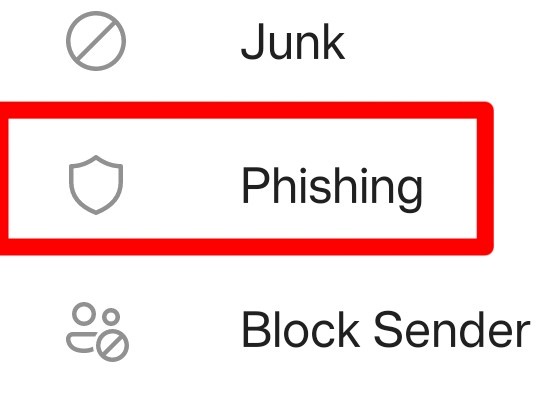
Tap Phishing
Tap Report if the Report junk message appears
- Passwords
-
Think strong for your account password! #ThreeRandomWords
Always use a strong and separate password for your UoA account.
When thinking of a strong password for your account the longer and more unusual it is the stronger it will be. But longer does not mean complicated. A good tip is to think #ThreeRandomWords mix in some numbers & special characters to make a strong and memorable password.
Do not use the same password across different accounts. If you are using the same password elsewhere, change it to keep all your accounts secure.
- Forgotten your password or want to update it? Please check out our Toolkit guide - Password Reset guide
- National Cyber Security Centre advice https://www.ncsc.gov.uk/
- Top Information Security Tips
-
The University's Information Security team has put together our top tips to help remind us all of the importance of information security in every aspect of our daily work. Information Security. We are all responsible.
Be aware it could happen to you
Don't ever say, "It won't happen to me". We are all at risk and the stakes are high - both for your personal and financial well-being and for the University's standing and reputation. If you are looking for advice, contact us.
Protect your password
Keep your passwords unique and strong. Do not share them (not even the Service Desk will ask you to reveal your password). Consider using a password manager. Find out more about strong passwords. #ThreeRandomWords
Phishing - think before you click
Curiosity, urgency, fear and greed are just some of the tactics used to get you to bite! Find out more on how to spot and report a phishing email.
Use Multi-Factor Authentication on critical accounts
Multi-Factor Authentication (MFA) helps secure your account with something you know and something you have. Enable MFA on all your accounts if available. It is required for your University account. Find out more about MFA for your University account.
Keep up to date with your training
Complete your online mandatory training for Information Security and Data Protection to help you keep informed. Find out more about our training on the MetaCompliance platform.
Use mobile devices safely
Many of us use a mobile device for personal and work life. They can hold a surprisingly large amount of personal and sensitive data. Make sure you are protected.
- Ensure PIN or password protection for your device is turned on.
- Turn on device encryption if available.
- Keep the device's operating system up-to-date.
- Avoid accessing or storing personal information on the device.
Find out more about staying secure when travelling with your devices.
Consider physical security & always lock your devices
The physical security of your devices and work area is just as important as technical security. Lock before you walk.
- Apply your device's screen lock whenever you leave it unattended, even for a short period of time.
- Secure and lock your work area if you can.
- If entering a secure area that requires swipe card or key access, be mindful of tailgaters trying to follow you in.
- If you keep protected data on a flash drive or external hard drive, make sure it is encrypted and locked up. Find out more about encryption.
Keep software up-to-date and use anti-virus
New malware and viruses are released every day. Protect yourself.
Back up your data
Back up your University and personal data regularly.
Find out more about University data storage & archiving.For help and advice contact IT Services via MyIT myit.abdn.ac.uk or email:
servicedesk@abdn.ac.uk . - Encryption
-
It is mandatory that you encrypt any USB flash drive and/or other portable device that contains sensitive University data.
If you don't, you risk not only accidental loss, destruction or damage to data but also unauthorised disclosure of confidential, personal, or commercially valuable data.
What is encryption?
Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
Encryption encodes data so that it can only be read by someone who has the right encryption key (password) to decode it.
This means that if your device is lost or stolen, the information contained on it cannot be accessed by unauthorised users.
Do you need to use USB?
While encrypting your USB device can protect the data on it from being accessed by unauthorised users, it cannot protect the device itself from being lost, stolen, corrupted or physically damaged.
- Never use a USB device as your only method of storing and backing up data.
Consider the secure alternatives
- Network drives - your H: drive or shared departmental drive is the most secure location for your data - as an area of managed filestore it is fast, reliable and secure. The servers are backed up onto tape nightly and, in an emergency, these tapes can be used to restore files that have been lost or damaged.
- VDI - provides secure, authenticated access to your H: drive and shared network drives when you are off campus via your personal device; all you need is an internet connection.
- Direct Access - connects your University owned and managed Windows laptop directly to the University network whenever you are off campus and have an internet connection.
-
File Transfer service - one and a half times faster than email, this web-based service is a secure and simple way to send and receive files of up to 20GB in size. The service can be used by University of Aberdeen staff and students and colleagues outside the University making it the ideal solution for researchers who need to exchange files securely with external collaborators. Find out more about our file transfer service.
- Email - don't forget that email can provide a convenient method of transferring smaller files, up to 25MB including attachments.
- Out of Office - Security Considerations
-
Outlook's Out of Office automatic reply is a helpful feature for informing colleagues that you are out of the office and when you intend to return. However, automatic replies can reveal a lot about us, and innocuous snippets of information can be really useful to cybercriminals engaging in phishing and social engineering.
What information can be revealed?
Cyber criminals and spam bots send out messages looking for a response. When an automatic reply is received, this alerts the sender that an address is active, immediately making it a more viable target.
The automatic reply can also reveal whether an email address belongs to an individual or is shared. If a signature is included, the cyber criminals may get phone numbers and physical addresses too.
We often include additional information within our automatic replies, such as the duration of our absence and whether we are on holiday or a business trip. Besides that, we may include alternative contact details, sometimes revealing information on work projects and internal team structures.
All this information can be used to craft highly targeted and plausible phishing campaigns.
What can you do to reduce the risk of attack?
- Where possible, only enable internal automatic replies (Inside My Organization) to provide University colleagues with useful information regarding your holiday, absence or out of office status.
- If you are in communication with a few key external contacts or vendors, it is safer to warn them of your absence directly and ahead of time.
- If you do need to enable external automatic replies, consider the following guidance:
- Create a separate message, and include as little information as possible
- Avoid naming colleagues and providing their job titles and contact details. It is safer to include an appropriate shared mailbox, if available.
- Do not include any details of your activities or whereabouts and, where possible, avoid including the duration of your absence.
- Do not include your usual email footer in your automatic replies.
- Mobile Device Security When Travelling Abroad
-
The best way to protect your personal devices and data is to leave them at home. If you don't need it, don't take it.
Consider using a cheap phone for the trip, particularly if you intend to get a local SIM card. After your trip, reset or dispose of it thoughtfully, and never store sensitive information on it.If you choose to take your personal device when travelling abroad, here are some steps and advice for you to consider.
Protecting your device before you travel
There are several settings you can enable or disable, and actions you can consider before you travel.
- Back up your device and your files.
- Remove your sensitive data from the device.
- Turn on device encryption if available.
- Confirm your device's operating system and apps are fully up-to-date.
- Ensure PIN or password protection for your device is turned on.
- Turn on your device's screen lock time-out and set it to a minimum time.
- Turn off Wi-Fi, Bluetooth and NFC.
- Turn off auto-connect for Wi-Fi and Bluetooth.
- Turn off wireless device to device sharing, such as AirDrop on iOS or Nearby Share on Android.
Physical Safety
Always keep your devices on your person whenever possible.
- Do not put them in your check-in baggage.
- Do not assume your device is safe in your hotel room, even in a locked safe.
- Do not lend your device to people you don't trust.
- Be mindful when using your device in a public space. Take care that your screen is not visible and no one is attempting to view it, sometimes called 'shoulder surfing'.
Virtual Safety
If you must use Wi-Fi, be cautious of using insecure Wi-Fi. Don't have any expectation of data privacy on public Wi-Fi, hotel Wi-Fi or in internet cafes.
- Consider using a Virtual Private Network (VPN) on your device, especially if you are accessing the internet.
- Only turn on Wi-Fi, Bluetooth and NFC when needed. Turn them off at all other times.
- Do not use public Wi-Fi to make online purchases, access bank accounts or other sensitive data.
- Avoid using work-related services and applications on your device where possible.
- Be mindful when accessing your email and do not open emails from unknown sources.
- Supplier Assessment
-
The University must ensure personal data is protected by our suppliers and that our information is given the appropriate level of security. Third parties that process information on our behalf must be vetted and accountable to the University under a contract.
Full information on the Supplier Cyber and Data Assessment process are on the Data Protection StaffNet page.
- Use of Messaging Apps
-
For guidance on use of messaging apps, such as WhatsApp or WeChat, please see our guidance document below (staff and student access only).

